Impersonate Autotask Resources from TopLeft
Make changes in Autotask from TopLeft as if the user was making the change directly in Autotask
TopLeft supports Autotask resource impersonation. This allows a person to make a change to Autotask data from TopLeft as if the person made the change in Autotask. This has two benefits:
- The history for tickets, projects, time entries and other records shows that the Autotask resource made the change, rather than showing that the change was made by the TopLeft API user.
- Changes are subject to the resource's security level restrictions.
To enable resource impersonation, an Autotask API User should be added first.
Once your API user is configured, follow the instructions below. These steps must be performed by an Autotask administrator with permission to manage security levels and resources.
Configuring Autotask API User Impersonation
There are three steps to configure resource impersonation in Autotask:
- Set a security Level for TopLeft (API-only)
- Set a security Level for each resource
- Enable the impersonation setting in TopLeft
Set a Security Level for TopLeft (API-only)
Go to Autotask.
1. Open the ADMIN options from the drop-down menu in the top left.
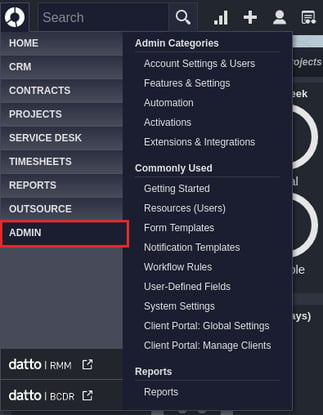
2. Under the Account Settings & Users tab, expand the Resources/Users (HR) section, then open the Security Levels option.
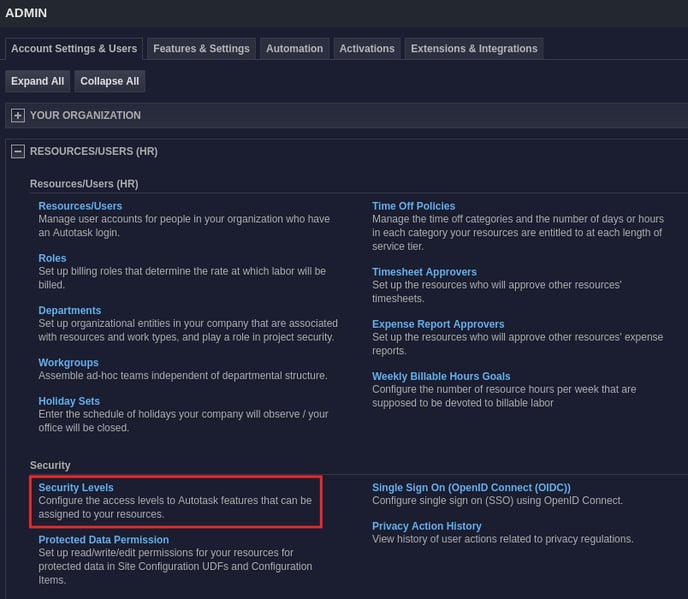
3. Edit the TopLeft Security Level created while configuring your Autotask API User.

4. Set WEB SERVICES API module's security setting as follows.
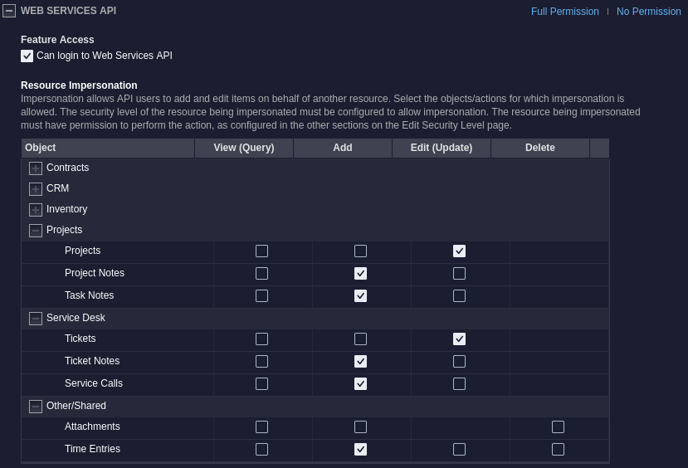
Module: WEB SERVICES API
You need to select the options listed below:
| Object | Description | View (Query) | Add | Edit | Delete | Comments |
| Projects | Projects | Checked | Enables resource impersonation for editing projects | |||
| Projects | Project Notes | Checked | Enables resource impersonation for adding project notes | |||
| Projects | Task Notes | Checked | Enables resource impersonation for adding task notes | |||
| Service Desk | Tickets | Checked | Enables resource impersonation for editing tickets. Note that resource impersonation for Checklist and Manage Resource isn't supported yet in Autotask. | |||
| Service Desk | Ticket Notes | Checked | Enables resource impersonation for adding ticket notes | |||
| Service Desk | Service Calls | Checked | Enables resource impersonation for adding service calls | |||
| Other/Shared | Time Entries | Checked | Enables resource impersonation for adding time entries |
Set up Resource Security Levels
Security levels applied to your resources in TopLeft must have the Resource Impersonation option checked to allow impersonation by an API user:
- Open the ADMIN options from the drop-down menu in the top left.
- Under the Account Settings & Users tab, expand the Resources/Users (HR) section, then open the Security Levels option.
- If you would like the user to have a system security level, right-click the desired security level, and click Copy Security Level. If it is not a system security level, skip this step and open the settings for that level.
- In the Web Services API section, select the following checkbox:
Resource Impersonation > Allow impersonation of resources with this security level
Turn On Impersonation in TopLeft
To enable impersonation, navigate to Admin > Advanced Options, find the IMPERSONATION option, and ensure the setting is enabled.

If you change the setting, click Save at the bottom of the page.
Autotask API Resource Impersonation Limitations
Autotask does not support resource impersonation for:
- Adding or editing checklists
- Editing tasks. (However, adding task notes is supported.)
Resource impersonation is supported for editing project status (shown in Autotask in the Notes section) and project notes (visible on the Activity tab).
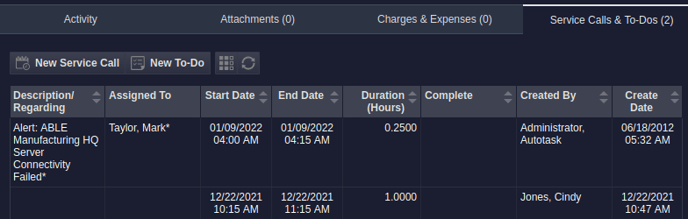
Resource impersonation is supported for creating service calls from TopLeft but Autotask shows the resource that created the service call in "Service Calls & To-Dos" tab, not in "Ticket History".
Autotask Security Level Limitations
- Security Levels for Resources copied from "Administrator", "Executive", or "Professional" have no limitations. They can be used on resources without any forced limitations from Autotask.
- Security Levels for Resources copied from "Team Member", "Co-managed Help Desk", or "Contractor" cannot use impersonation for some requests, no matter what settings are applied. These are the limitations:
- "Team Member" based security levels cannot:
- Edit Projects
- Drag Project cards
- Add Task notes
- "Co-managed Help Desk" based security levels cannot:
- Edit Tickets and Projects
- Drag Ticket cards and Project cards
- Add Task notes
- "Contractor" based security levels cannot:
- Edit Tickets and Projects
- Drag Ticket cards and Project cards
- Manage Service Calls
- Add Time entries on Tickets and Tasks
- Add notes on Tickets and Tasks
- "Team Member" based security levels cannot:
- Security Levels for Resources copied from "Time & Attendance Only" or "Dashboard User" cannot be used on resources that need impersonation. They will not be able to make any changes in TopLeft.
![White logo TopLeft_240x78.png]](https://help.topleft.team/hs-fs/hubfs/White%20logo%20TopLeft_240x78.png?height=50&name=White%20logo%20TopLeft_240x78.png)